Cyber Threats Facing the US
( Oleg Reshetnyak / Associated Press )
Brian Lehrer: It's The Brian Lehrer Show on WNYC. Good morning again, everyone. With two wars going on right now that the US is involved in and a contentious election year upon us in which both parties are raising fears of electronic tampering in one way or another, not to mention the generalized anxiety disorder we're all suffering from these days regarding artificial intelligence and what it might bring, we have a rare opportunity now to speak with the head of US Cyber Command, General Paul Nakasone.
General Nakasone must have three very big heads because he wears three very big hats, commander of Cyber Command, director of the NSA, the National Security Agency, and chief of the Central Security Service. His whole career of almost 40 years has been spent in military intelligence, including overseas in Afghanistan, Iraq, and Korea, and at high levels in the Pentagon. I don't know whether to call you commander, director, or chief, so I'll just say General Nakasone, thanks for some time today, and welcome to WNYC.
General Paul Nakasone: Brian, thank you very much and it's nice to be back in New York City. Thanks so much for your time today.
Brian Lehrer: Before we get to the issues, can you introduce yourself a little to our listeners and describe briefly with these three hats, and I presume not much time to sleep? What are your work days like? What is it basically that you do?
General Nakasone: Brian, I'm a career army officer. I've served around the world and peace and war, including the Pentagon on 9/11. Today, I lead two very large organizations, very important organizations. First of all, the National Security Agency, with really two primary focus areas, signals intelligence and cybersecurity. We produce foreign intelligence and we defend the nation's classified networks and warfighting systems. At US Cyber Command, we're all about offensive and defensive military operations in cyberspace.
We focus on the Department of Defense's network and also our data and weapon systems for the nation. You would say, "Why does this matter?" It matters because think about the importance of being able to understand what our adversaries are going to do and also think about cyberspace. Think about what cyberspace means to every single person in New York City, our nation, and the importance that it is to our national security and our economy.
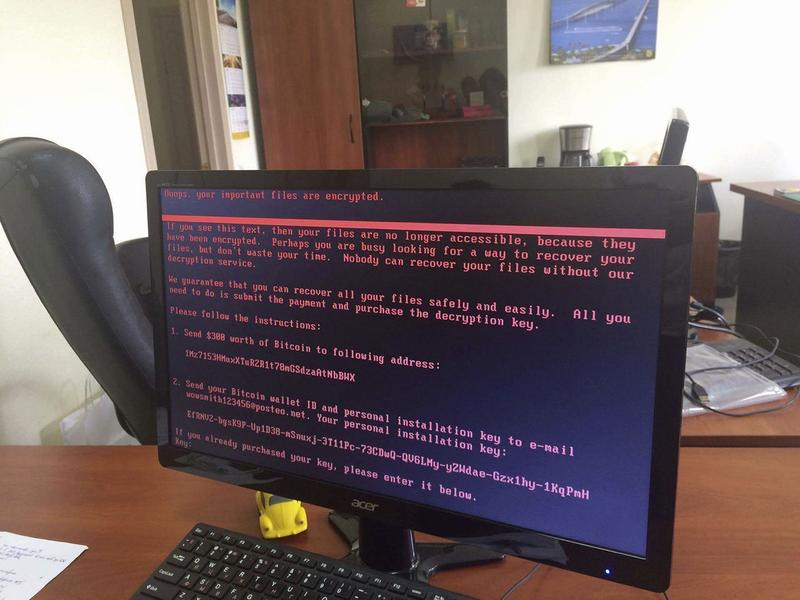
Brian Lehrer: We'll get to as much as we can of Israel, Ukraine, AI, and our 2024 election security in this respect. I wonder if you tell our listeners the story first of what's been described as the largest publicly disclosed cyber attack against critical infrastructure in the United States. This was not such a New York thing. Some of our most local listeners may not remember it, but it was just three years ago in 2021, the ransomware attack on the colonial oil pipeline that affected gasoline and other fuel supplies, mostly in the Southeast, I believe. With almost three years of hindsight, who did what to a critical part of our energy infrastructure and why?
General Nakasone: Brian, great question. Before I talk about Colonial Pipeline, let's talk about 2021 and the importance to the nation because 2021 introduces this idea where I say cybersecurity is national security. We begin the year with not Colonial Pipeline but solar winds. Remember, this is a Russian supply chain attack into our infrastructure. By May, we understand that there are hackers that are impacting the Colonial Pipeline.
The importance of the Colonial Pipeline, 43% of our petroleum products on the East Coast are traveling through this pipeline. This is impacting us. Then by the summer time frame, we also have a number of attacks against food distributors. In one year, we've had supply chain. We had ransomware. We had zero-day attacks against our critical infrastructure. I would tell you. I think that since that time, a tremendous amount of progress that our nation and I think the Department of Defense has made to ensure the [inaudible 00:04:03] infrastructure.
Brian Lehrer: You called that one Colonial Pipeline, a ransomware attack. Did they ask for and receive money from the company? Was that the point?
General Nakasone: They did, Brian, and that was the whole idea. It's the criminal act by a series of actors operating outside of Russia to try to elicit money, which they receive from the company, in terms of being able to impact critical infrastructure portion of the United States.
Brian Lehrer: Ransomware, from what I see reported, is becoming increasingly common despite the steps that you've taken since 2021. Just looking at the news from the last day, which I did to get ready for this conversation, the mortgage and lending company, loanDepot, announced just yesterday that it's been hit with a ransomware attack.
The Financial Times reported yesterday on the British Library system facing at least six million British pounds in expenses, it's about $6 million, from a recent ransomware attack. The Toronto Zoo, of all things, says it was hit with a ransomware attack on Friday. It assures us that the animals were not affected. From the finance industry's loanDepot to two cultural institutions, a library system, and a zoo, and in three different countries, this is going on. What ties these all together?
General Nakasone: What ties these all together is the fact that the way that we get after ransomware is through partnerships. This is a partnership between the National Security Agency and US Cyber Command and us with FBI and Department of Homeland Security and, most importantly, with the private sector. Being able to work here is a partnership that must take place and this is one of the areas that we work very hard on.
I think the other thing that's really important to understand, Brian, and we get into this, is what's the individual user on a computer system? What's their responsibility to avoid ransomware in the future? I'm more than happy to talk about that, but this is a collective effort. This is the world in which we live in and this is the competition that we must be collectively prepared to address.
Brian Lehrer: Do talk about that. I'm sure our listeners would like some advice. If I run a business or a library or a zoo, what should I be doing to protect against ransomware?
General Nakasone: The first thing is strong passwords. You have to have strong passwords. The idea of using the same password for multiple accounts, really bad idea. The second thing is the most transformative technology of our lifetime has been the smartphone. Being able to update that operating system is the second thing we should always do. Third piece is two-factor authentication. Make it as hard for criminals to get into your account as possible. Two-factor authentication is it. The last piece I would say is, hey, a bit of the appeal in terms of how an actor or a criminal is working to hook you is through high-pressure tactics. Breathe. Read it. Figure out that, "Hey, does this make sense?" If it doesn't, don't act on it.
Brian Lehrer: Let me go on. Listeners, we can take some phone calls for the head of US Cyber Command, General Paul Nakasone. Your questions are welcome about potential cyber threats, foreign or domestic, to American individuals and businesses and cultural institutions, as well as the military or how to protect yourself or your business. You can ask about US policy in the cyber war era as well, 212-433-WNYC, or on the elections to come if I didn't mention that specifically, 212-433-9692. Call or text.
General, let me go on to cybersecurity in the elections. I see that just a few months ago in October, the government released an intelligence assessment about Russian election interference. Quoting from Reuters coverage of this, it says, "The assessment found Moscow is using spies, social media, and Russian state-run media to erode public faith in the integrity of democratic elections worldwide." It continues that, "In 2020, Russia's FSB security service secretly worked to intimidate election workers, organize election-day protests, and sabotage overseas voting in an unnamed European country's 2020 election." My question is, what about our elections in 2020 and 2016?
General Nakasone: Yes, so I would say, first of all, that this is our fourth election for the National Security Agency and US Cyber Command working to defend what we see as critical infrastructure for us. We've had success against Russia. We've had success against Iran. We've had success against China. It's the same methodology that we used, Brian.
First of all, being able to gather insights and understand the adversary better than they understand themselves. Secondly, being able to share intelligence, share intelligence with Department of Homeland Security insisted that has the responsibility for state and local elections, and the FBI. The last piece is to contest any type of adversary that's going to try to interfere or influence our elections. This is what we've done in '18 and '20 and '22 and what we'll do in '24 as well.
Brian Lehrer: What's your role at Cyber Command and in protecting our elections this year, or as part of the military, don't you do domestic stuff?
General Nakasone: We don't. We're outside the United States. We operate against foreign adversaries. This is the ability to understand both from the National Security Agency, what our adversaries are doing, and then be able to take action against these adversaries. Again, this action might not necessarily be just the Department of Defense. It might be with the Department of Defense and the Department of Justice or it might be with a series of other government actors or even the private sector. Being able to shine a light on this type of malfeasance is exactly what we do and what we do very well.
Brian Lehrer: After the 2016 election, there were reports of not just Russia attempting to destabilize all democracies, but teenagers in Macedonia because they made money at it online spreading fake stories that Americans then shared on social media, most of them reportedly anti-Hillary Clinton, because that's where most of the money turned out to be compared to anti-Trump social media stunts. Did your assessment look at that and with an eye toward this year?
General Nakasone: In looking at every single election back to '16, one of the things that we certainly see is that there is a component of nation-state, which we talked about what Russia is trying to do, but there's also a criminal component of this. This is why it's so important that we operate with a series of partners like the FBI, like DHS, and CISA to be able to understand what they're doing overseas and then being able to share that information.
Brian Lehrer: Was there any cyber attack element to January 6th or the stolen election lie in that post-election period generally?
General Nakasone: Nothing that we've been able to determine there, Brian, in terms of what we've seen.
Brian Lehrer: Are cyber attacks a factor in either the war in Ukraine or in Israel and Gaza?
General Nakasone: Certainly, cyber operations are ongoing all the time. You may recall in the first couple of days of Russia-Ukraine when Viasat was taken down, the ability for Ukraine to operate with their commercial communications capability. Here's the interesting thing is that Ukraine understood that that wasn't the only way they could communicate. Then being able to bring a private sector company and being able to communicate is what they've done so effectively. It's also been an element of what we've seen in Israel-Hamas being able to create stories, being able to spin a narrative that Hamas did in the early days of 7 October.
Brian Lehrer: Some of the ways President Biden has been critical of Israel for what Biden called indiscriminate bombing and Defense Secretary Austin, who would be your boss in a similar vein, I wonder for you as head of Cyber Command, are there cyber techniques that they could be using for more precise ways to dismantle Hamas' fighting infrastructure without so much killing of civilians?
General Nakasone: Well, certainly, there's a full spectrum component in terms of what goes on. I think it begins, first of all, is understanding what your adversaries are doing. That's one of the things that we do so well at the National Security Agency. What are these type of actors trying to do and are they having success at it?
Brian Lehrer: Let's take a phone call. Here is Michelle in Middletown. You're on WNYC with the head of US Cyber Command, General Paul Nakasone. Hi, Michelle.
Michelle: Hi, Brian. Thanks for taking my call. Hello. What I'm curious about is this time of year, it appears that I'm getting a lot of notifications from companies that I totally forgot that I subscribed to or that I have an account with, that my account has been compromised, and that I should change my password. I'm doing that, but what I would really like to do is 100% just delete my account or unsubscribe totally. A lot of these sites don't make it easy for you just to delete your entire account because they force you to create an account even if it's a one-time purchase. We end up with hundreds of accounts that we only use one time, but our information is still out there. I want to delete all of them. Is that possible?
Brian Lehrer: General?
General Nakasone: I guess, Michelle, I would have to refer to the actual company. I'm not sure exactly their policies, but I do come back to this idea. I think you hit the concern that I have is that as you think about online and operating online, begin with this idea of you can't have the same password for every single account. We see far too much of this in terms of the reporting that goes on. The other thing is really understanding if you're going to make an account, having two-factor authentication, incredibly impactful in being able to protect yourselves.
Brian Lehrer: Michelle, I hope that's helpful. We talked about the worst publicly-announced cyberware attack against critical infrastructure in this country, the Colonial Pipeline attack. What about cyber attacks staged by the United States? I imagine as head of Cyber Command, you play offense, not just defense. In fact, I think you said that when you were introducing yourself at the beginning.
General Nakasone: Brian, we don't necessarily talk about our ongoing operations, but yes, we have a full-spectrum capability. You should anticipate that as part of our department, when we're asked to do things, we do things based upon civilian control of our military by the law of armed conflict in a lawful manner. It's one of the things that we look at constantly and plan for.
Brian Lehrer: Back in 2012, for example, The New York Times reported on the computer worm known as Stuxnet, which was reported to be a joint US-Israel operation that crippled part of Iran's nuclear infrastructure. Stuxnet devised during the Bush administration, unleashed under Obama. How do you look back on Stuxnet in particular?
General Nakasone: Again, I think, Brian, the important thing here is that we look at all different type of capabilities as we look back and make sure that we understand what was effective and what wasn't effective and what our adversaries are doing. That's how we really judge in terms of what's going on.
Brian Lehrer: If we are waging cyber war, can we be so upset at our enemies when they waive cyber war?
General Nakasone: Brian, one of the things that I think is most important is that our mission is to defend the United States. We defend the United States in a manner that is consistent with our values, consistent with our laws, and consistent with our policies. That's what we're held to and that's what we do every single day.
Brian Lehrer: Matthew in Manhattan, you're on WNYC. Hi, Matthew.
Matthew: Hi. Thanks for taking my call. I recently saw a movie with Julia Roberts called Leave the World Behind. The concept was that hackers took down the satellites above the United States and basically turned us into a dystopian world. I'm not sure if you saw this or heard about it, but I didn't know if that's possible like a concerted attack by China, Russia, that sort of thing.
Brian Lehrer: Did you see Leave the World Behind, General?
General Nakasone: I guess I've been too busy in what I've been doing on a daily basis to see the movie, but I would really like to comment on the question, which is I think the importance of what we do on a day-to-day basis. It does begin with defense and being able to understand and being able to secure our most sensitive communications and our most important weapon systems. That's what we do at NSA and that's what we do at Cyber Command.
To prevent what this movie's plot is, is something that we think a lot about, but it's also not the sense that we're doing everything. It's done with the partnerships that exist within our government and most importantly, critically, what the private sector does, right? The importance in terms of being able to secure their data and their networks is foundational to their success as well.
Brian Lehrer: Andrew in West Orange, you're on WNYC. Hi, Andrew.
Andrew: Hi there. Thanks for taking my call. My biggest concern is going to go back to the topic we covered a little earlier around the 2024 election cycle. My concern is about artificial intelligence and its ability to, if you will, create very plausible misinformation, which is already taking place, but I'm just concerned it's going to explode in the next election cycle. What's going to be done to mitigate that?
General Nakasone: I think that's one of the key pieces you speak to, generative artificial intelligence. We think about the large language models that are being used today. One of the things that has to be done is that we have to understand not only what we're doing as a government, but also what the private sector is doing. That's what we do very effectively at NSA and also at Cyber Command, being able to understand, "Hey, these are the limitations," and then being able to communicate that.
One of the things that has changed in the way that we do our work is the fact that we do so much of it in an unclassified manner and being able to release this to the public. This is what we do with cybersecurity advisories. This is what we will do to protect artificial intelligence. That's one of the areas that we've stood up at the National Security Agency is this idea of an artificial intelligence security center and identifying the challenges and the gaps and the activities of what our adversaries are doing.
Brian Lehrer: Here's a follow-up question and I hope that was a helpful question, Andrew. Actually, let me follow up on it a little bit because we know, certainly, in the 2020 election period and for most of the last few years, the FBI considers domestic terrorism to be more of a threat than foreign-based terrorism and largely coming from the right in this country. Again, I don't know what you can do as part of the US military. Maybe because the military is not supposed to act domestically, you can't do anything. With all the knowledge that you have about cybersecurity, is there anything specific that you can say about how you're working to protect the integrity of the American electoral system this year?
General Nakasone: Brian, you're correct. Our focus is on foreign adversaries. Let me give you an example. In 2020, we noted that the Iranians were attempting to release videos that purported some type of election problems on the day of the election. What do we do? We release this information with the director of FBI and the director of the National Intelligence. The way that you get around that is shine a light on it. Shining a light means that you understand what your adversaries are doing. That's what we do very, very well at NSA.
Brian Lehrer: I saw, by the way, that the assessment that came out in October said Russia is trying to destabilize democracies all over the world. China, for whatever mischief it causes, is not. Is that your understanding?
General Nakasone: It's interesting. You look at, right now, what the Russian mode of operations is. This is a for-profit undertaking that we've seen private military companies from Russia actually go to different nations and talk about being able to rig your election. We see this. We report on it. We were able to expose it. We see with regards to China's past behavior, it has been very targeted against very select elections. As we look at this for '24, we start with that baseline. We're looking to confirm or deny that.
Brian Lehrer: How can an individual protect themselves against disinformation that may be Russia-generated?
General Nakasone: I think that with anything, it begins with an understanding, right? You begin with a personal understanding of an issue, not being able to go to one sole source, and look at it and accept that that may necessarily be the answer. It's like writing a research paper, right? There's not one source that you're going to utilize to write that paper, but you're going to use a multitude of sources. Being able to understand those sources and to question what you might be seeing and hearing is important.
Brian Lehrer: Here's a follow-up in a text message from a listener to what an earlier listener was asking you about regarding companies telling her to change her password because it's been compromised. This listener writes, "Often when the company is asking for us to change our passwords, it's not actually the company. It's a phishing attempt. Can the guest please speak to that when it's not actually the real company?"
General Nakasone: It's exactly what that criminals are doing to garner this type of access to your accounts. Anytime you receive an email like that, you should be highly suspicious. Companies just don't do that. That is a trick that we've seen utilized by a number of different actors for a number of different years. That's really to the point, Brian, that I said is when you see these things, take a second. Breathe. Think about, "Does this make sense?" It probably doesn't. If it doesn't, don't do it.
Brian Lehrer: Donald in Jackson Heights, you're on WNYC with General Paul Nakasone, the commander of US Cyber Command. Hi, Donald.
Donald: Oh, hey, Brian. Thanks for taking my call. My question is about recruitment and how you go about recruiting really smart people when your competition is ultimately involved somewhere in the private sector with companies like Amazon and Google. Obviously, they're going to be offering a lot of money. Is that something that you find challenging and are you able to get the candidates that you need?
Brian Lehrer: Great question. How about recruitment in this area, General?
General Nakasone: Brian, I would tell you. To begin with, the question is spot-on. Do we get the candidates? You bet we get the candidates. Why do we get those candidates? This year, we're going to hire 2,500 people at the National Security Agency. 300 people at US Cyber Command will get those numbers. What makes a difference for us, first of all, is the mission that you're going to do.
You're not going to come to the National Security Agency or US Cyber Command and come for money, but you are going to come for mission. It's the place where you're going to do incredible mission working with our best technology and I would say our best people. If you think about election defense, if you think about securing the nation, this is contagious for people that work here.
What's our job? Our job is to ensure that that culture remains. We also have the responsibility to look throughout the nation. Look for our talent, not only on the East Coast but in the Midwest, the West Coast, and the South. Everywhere we can go. It's one of the things that I do a lot of is ensuring that people know that, "Hey, there's an opportunity," just by going on nsa.gov or uscybercom.mil to understand what the future holds for you.
Brian Lehrer: We're just about out of time and I know you got to go. One more follow-up on the personal side from a listener who texts, "How are password managers--" like many of us have on our devices, the password managers, "How are password managers impervious to hacking?"
General Nakasone: Nothing is impervious to hacking. We've seen this in terms of companies that are hacked. I would tell you, much in the same way, you don't necessarily have to be the fastest. You just cannot be the slowest. Password managers are an effective way of looking at number of different ways to be able to secure accounts. Again, it's a layered approach, Brian. It begins with his idea of strong passwords. It's being able to update your operating system and it's also using two-factor authentication with a strong dose of common sense.
Brian Lehrer: General Paul Nakasone wears three big hats. He's the commander of US Cyber Command. He's director of the National Security Agency and chief of the Central Security Service. Thank you so much for talking about cybersecurity with us today. We really appreciate it.
General Nakasone: Thanks, Brian. Have a great day.
Copyright © 2024 New York Public Radio. All rights reserved. Visit our website terms of use at www.wnyc.org for further information.
New York Public Radio transcripts are created on a rush deadline, often by contractors. This text may not be in its final form and may be updated or revised in the future. Accuracy and availability may vary. The authoritative record of New York Public Radio’s programming is the audio record.

